If you send an app message to someone you know, it cannot simply be intercepted and read by third parties. Communication on WhatsApp is in fact secured by means of encryption, also known as encryption. These words fly by a lot in the news – but what do they actually mean?
What is encryption?
Encryption is a form of cryptography: the concealing or encrypting of a message by means of a code. Cryptographers convert a basic text (also called ‘plaintext’) into an encrypted text (‘ciphertext’), using a mathematical formula or algorithm. This formula is called a cipher.
One of the oldest ciphers has already been used by Julius Caesar: a secret code in which all letters of the alphabet are shifted a few places. Such a simple cipher, for example, moves each letter four steps backwards, making an ‘e’ an ‘a’ and an ‘f’ an ‘b’.
But such a secret code is fairly easy to crack, certainly with the help of today’s computer power. You just try out possibilities until you find out how the letters are shifted.
Classic ciphers such as those from Caesar are also easy to crack by looking at how often certain letters are used. The ‘e’, ‘n’ and ‘a’ are, for example, the most used letters in Dutch. The letters that appear most often in the text are probably one of these three letters.
How are my app messages encrypted?
Your WhatsApp messages are therefore not very well protected if parent company Facebook would just shuffle the letters of your message.Algorithms for these types of services are usually deliberately extremely complex, to prevent a computer from trying out all the possibilities in a short time and thus getting to your message.
To achieve that, computers with a cipher calculate a long string. The longer the series, the longer it takes to crack. These series are a kind of passwords that are called keys. With this password your message will be changed to an unreadable knit.
What types of encryption are there?
There are basically two forms of encryption: one that works with one key (symmetrical) and one that works with two keys (asymmetrical).
You can see the difference in the following way. Imagine: you send a message and put it in a safe, which you send to your recipient. You lock that safe with your key. The recipient has a copy of exactly that key. That person can use it to open the safe and thus read the message.
In the digital world, this form of encryption works fairly quickly. After all, a computer does not have to make too many complex calculations: you only work with one key.
This ‘symmetrical encryption’ is therefore often used to quickly encrypt large amounts of data. A good example is the AES algorithm, which is used, among other things, to protect files in the cloud. It does have one major disadvantage: anyone who knows how to get the key can access your data in this way.
That risk is made more difficult with the other form of encryption, which works with two keys. Imagine the same safe. To lock the safe, you use a unique key. The receiver has a different key, but it only works to open the safe that is secured with the other key.
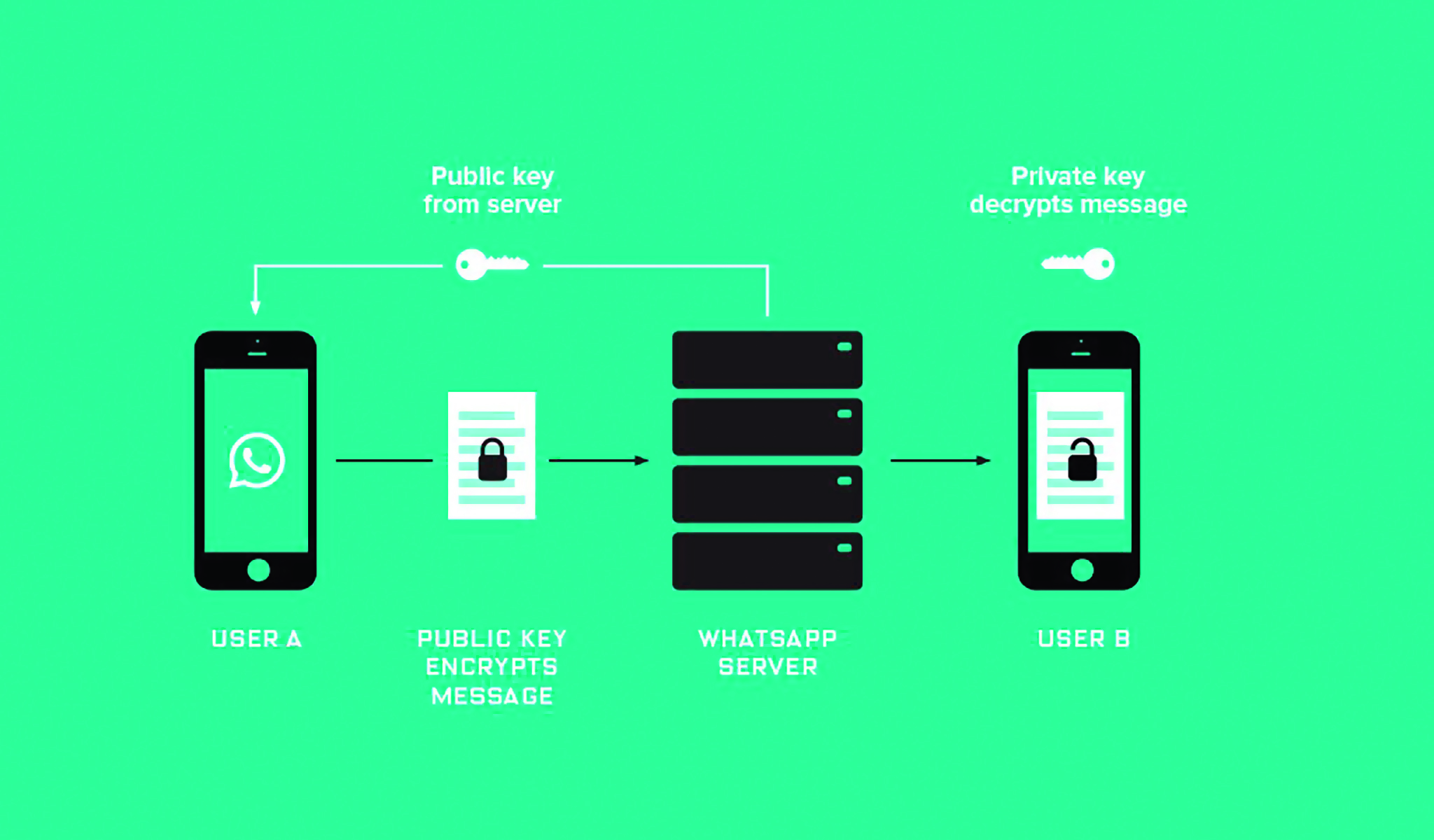
This form of encryption is called asymmetric encryption. In the digital world, the two keys are mathematically connected. For example, prime numbers are used for this. A public and a private key come from that calculation. You need both of them to communicate encrypted.
How do public and private keys work?
The public key is, as the name suggests, public and can be shared freely. Others can use this to convert a message to you into a line of seemingly random characters.
To get to the text afterwards, you need the private key: it converts the encrypted information into a usable form.
This process is slower than with a symmetrical key. The system must also calculate how the public key and the private key respond to each other. But if someone gets hold of your public key, he cannot decrypt anything with it. You do not share your private key with which you can.
What is end-to-end encryption?
Many apps, such as WhatsApp, nowadays use a form of encryption that is called end-to-end encryption. This is a strong form of encryption in which a message is encrypted from the start to the end point.
The content of the message is therefore not treated as ‘normal text’: the data remains encrypted on the road. In the case of WhatsApp, the message therefore passes through the company’s servers, but cannot be viewed by parent company Facebook.
That would be possible without end-to-end encryption. With Facebook Messenger, which does not use end-to-end encryption, a message is sent to a server, decrypted there, re-encrypted and sent to the sender. The content can therefore be requested via the server administrator.
So encryption is either asymmetrical or symmetrical?
No. Hybrid systems are quite popular because they can cope with many of the weaknesses of the two forms. You can even find the most famous hybrid here on NU.nl: HTTPS, a kind of website security that you can recognize by the lock for the internet address in a web browser.
In short, HTTPS works by first contacting your computer via asymmetric encryption and checking that it is you. In that ‘conversation’ it creates a symmetrical key, with which your data is then protected.
The encryption behind HTTPS is used to protect data sent by internet users. That way you can, for example, securely do banking, e-mail or send forms with sensitive data. Without encryption, its content would be easy to view for someone who knows how to intercept communication.